Thursday, 23 Jan 2025
8 min read
How to Add Two-Factor Authentication to Next.js SaaS Boilerplates
In this day and age, securing SaaS applications is at the top of the list. Especially if you are dealing with user data that is sensitive. However, one of the most effective techniques for security is usually 2FA, that helps upgrade the two-factor complement in applications. It has an additional secure cushion, which gives conditional access. As such, it becomes quite indispensable for Saas applications quite often housing personal as well as financial information.
Next.js is a React framework to create very fast and highly scalable web applications, making it a hit for SaaS development. Adding two-factor authentication to a Next.js boilerplate for SaaS stories may seem daunting in the beginning but with the correct steps, it can be coupled to your technology with no greater hassle. The present article shares the process of achieving two-factor authentication for a Next.js application effective in availing security on users and their data.
Table of Contents
- What is Two-Factor Authentication (2FA)?
- Why is 2FA Important for SaaS Apps?
- Prerequisites for Adding 2FA to Your Next.js App
- Step-by-Step Guide to Implement 2FA in Next.js
- Best Practices for Securing 2FA in Next.js Apps
- Common Challenges and How to Overcome Them
- Conclusion
- Frequently asked questions
What is Two-Factor Authentication (2FA)?
Two-factor authentication (2FA) is about adding that extra security layer for your online accounts, making the hacker's job a whole lot more troublesome. This is because normal authentication techniques aim for username-password pairs. In the 2FA method this, to validate user identity, requires two factors. The first factor would usually be something the user knows, i.e., a password. The other factor is something that the user has-like something that reflects the smartphone, or an authenticating app.
So, for example, if a user logs in afterward with a username/password, he can then be required to take a one-time passcode (OTC) that was sent to his mobile phone from him or generated by his authenticator app. Hence, even if a hacker could get as far as hacking a user's password, then the hacker still must have the second factor to enter by.
Why is 2FA Important for SaaS Apps?
SaaS apps have to handle a range of critical information types such as personal information, financial data, as well as operational information that should be maintained strictly confidential. Given the increasing incidence of cyber crimes by which online platforms have become highly susceptible and vulnerable, such data are key to protect. 2FA greatly reduces the potential to carry out storage from unauthorized access to the data, thereby offering both the user and the service provider mutual ease.
These days, more number of users look forward to added security features on SaaS platform with the news setting off the alarm on data breaches. 2FA can thus increase the security posture of your company and gain trust from users-as well as it required for some applications to have such a legal requirement since they store highly sensitive information, such as healthcare or financial applications.
Prerequisites for Adding 2FA to Your Next.js App
Before you dive into implementing two-factor authentication, there are a few prerequisites you should have in place:
- User Authentication: Ensure your app already has a robust user authentication system (e.g., using JWT, Passport.js, or Auth0).
- Backend Server: You'll need a backend to handle API requests related to 2FA, such as generating and verifying one-time passcodes (OTPs).
- SMS or Email Service: To send OTPs, you'll need to integrate a service like Twilio (for SMS) or an email provider like SendGrid.
- Authenticator App (Optional): For a more secure and efficient 2FA solution, you may want to integrate an authenticator app like Google Authenticator.
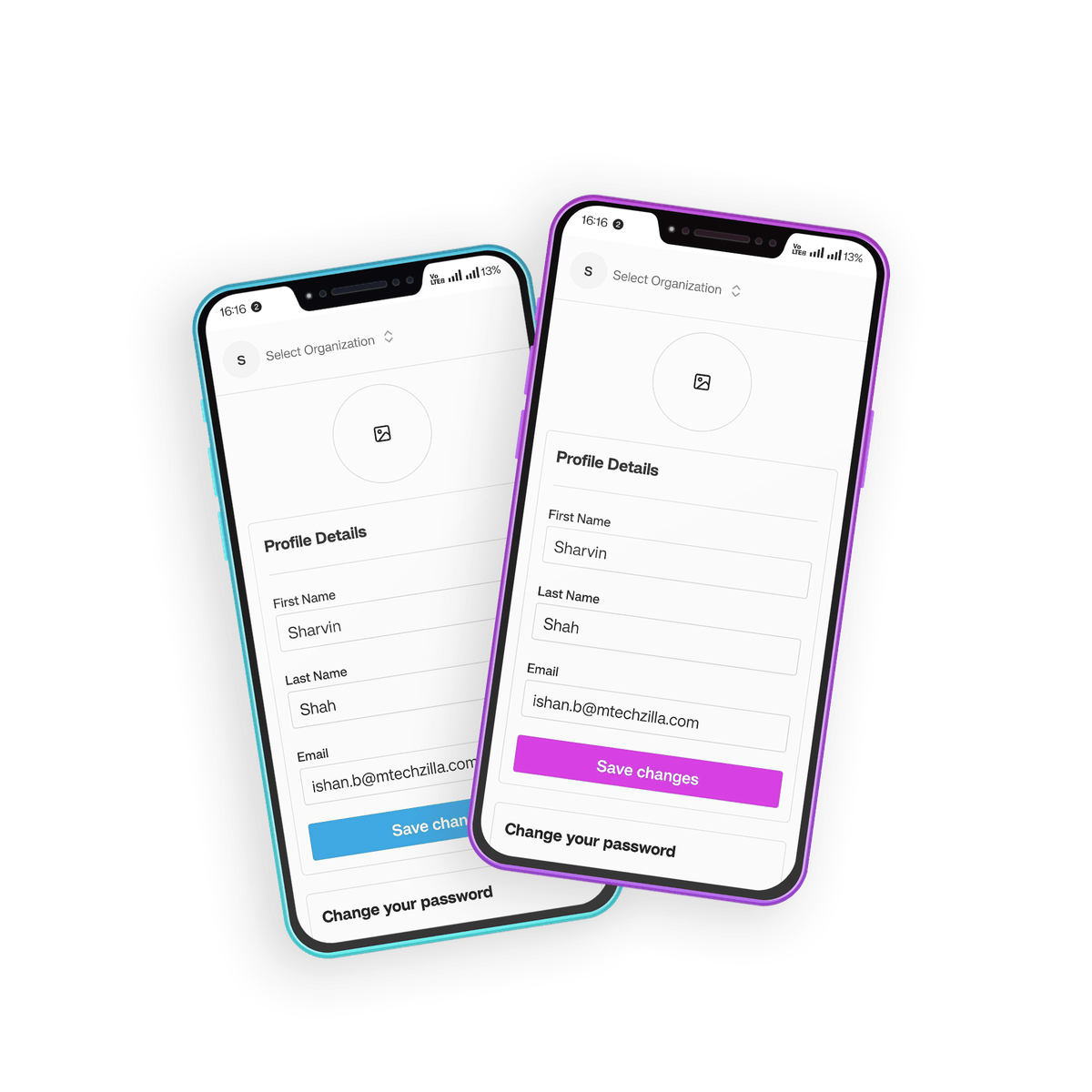
If you’re using a boilerplate like useSAASkit, you already have 2FA integrated, as it comes with user authentication and features like 2FA.

Step-by-Step Guide to Implement 2FA in Next.js
Integrating Auth0 for 2FA
Creation of an account on Auth0 and installing Next.js allows this last app to work correctly on Auth0. You need to combine both Auth0 and Next.js, a two-factor authentication-based solution to avail them in the application without the necessity of building them from the start. Here's how:
- Set up Auth0: Start either by setting up a completely new application or creating it in the Auth0 environment. Your Next.js application will involve tuning whether you need to write your Auth0 credentials, that is, client ID and secret.
- Install Auth0 SDK: Install the Auth0 SDK for Next.js by installing npm or yarn
npm install @auth0/nextjs-auth0 - Configure Auth0 in your app: Form an Auth0 configuration file and establish routes about that matter for authentication.
- Enable 2FA in Auth0: Visit the Dashboard and click Multi-factor Authentication under Main. Select 2FA among the alternatives that could be using SMS or an authenticator app.
Once successful, you are only a few steps away from having 2FA added to your Next.js app.
Implementing SMS-based 2FA
For SMS-based 2FA, services like Twilio could help in sending OTPs to the users' mobile phones. Below are the steps you can undertake to enable SMS 2FA in Next.js:
- Set up a Twilio account: Firstly, you should create an account on Twilio and fetch its API credentials that are Account SID and Auth Token.
- Install Twilio SDK: Install the Twilio SDK using npm:bashCopynpm install twilio
- Send OTPs via SMS: In the back end, you are going to use Twilio API to provide OTPs to users as soon as they set foot on your website. Save those OTPs to a temporary location within your database so you can verify them during possible login attempts.
- Verify OTPs: After someone keys in the OTP, all you need to do is compare the one stored in the database and allow their access in case of a match. Should it come down to invalidity, just tell the system to reject the login.
Using Google Authenticator for 2FA
Google Authenticator is very common for creating the user time-based one-time passwords (TOTP) to authenticate them safely. It allows the use of Google Authenticator and Next.js into the integration:
- Install a TOTP library: Some library, such as
speakeasycan be used for creating and validating OTPs. Installation can be by npm:bashCopynpm install speakeasy - Generate a secret key: Using the
speakeasy, throw up a QR code for a user to scan with Google Authenticator and use this library while the user decides to go to 2FA. - Verify OTPs: After a user logs in, they'll be prompted for the OTP which is created by Google Authenticator and needs to be checked through the
speakeasylibrary.
Best Practices for Securing 2FA in Next.js Apps
Two-factor authentication is one of the methods which could be used to increase the security of the applications. Even here, one needs to include various other things to ensure that the best of security practices are being used for both the clients and user interactions:
- Use Strong Passwords: The use of 2FA will not be efficient at all if the passwords used for 2FA are weak and boring at the same time. It should guide the user to follow strict password complexity policies as well guidance on the use of password managers in storing their credentials securely.
- Store OTPs Securely: Don't save the OTPs in your database in full text forms and always hash the OTPs before storing them. This will prevent any leakage of sensitive information.
- Mandating The Timeouts For OTPs: OTPs should have an expiry after 5-10 minutes so that the system should be according to the timer just in time usage of them. This way the OT P will be ineffective if someone gets access even to an OTP within a few seconds of its issue.
- Audit and Monitor 2FA Logs: With the regular auditing on events linked to 2FA, system teams could be improved. This could be with the likes of the failed OTP attempts, login anomalies or changes to the 2FA settings of a user. It can also make it possible to detect early majuscule-suspicious active accounts, enabling action to be taken before damages might occur.
Flanking your Next.js SaaS application with these best practices will help most out of two-factor public key infrastructure by the improved layering security from unauthorized access.
Common Challenges and How to Overcome Them
Implementing a two-factor authentication (2FA) is a great way to boost security, but it can sometimes bring challenges with it. Here is a list of the kind of problems you might face and a way to solve them:
- User Confusion: 2FA tends to confuse a number of users who are unaware of it. A good medium to unpack this is to offer simple, easy-to-understand instructions and an efficient customer service line that will help users to configure and use 2FA.
- SMS Delivery Issues: 2FA via SMS can fail once in a while in the network, which may lead to the interruption of the OTP receiving process. It might be worth considering using another form of authentication, such as Google Authenticator, which skips the SMS issues and provides a smoother user experience for SMS-related delivery problems.
- Backup Codes: Users may, from time to time, misplace their phone or authentication app through which they would otherwise access their accounts. If they have other ways to get into the account as soon as they enable 2FA-tool generation backup access codes: for employees who misplace their authentication mechanism or smartphone ensure that they will not get locked out.

Conclusion
It would enormously multiply both the high security of the application and safeguard the sensitive data held by the user. The source of 2FA comes as an added shield since it demands that an extra verification be carried out whenever the password is found to be stolen, thus minimizing the chances of access being allowed to an external party.
It can be easily merged into your app through several possibilities. This includes using Auth0 to run the input code, which is quite convenient and direct, or opting for SMS-based verification from services like Twilio and having OTPs sent directly to users or, if they've yet to support it, maybe look at rolling that option out or opting for Google Authenticator for TOTP that is time-based. Each method has its advantages; SMS would be accessible to everyone, Google Authenticator is more secured and cannot be compromised. Moreover, a great advantage offered by using 2FA is that it protects users. This mostly ensures a consistent culture of complying with the best practices for security.
Adding 2FA is cardinal to ensuring overall security and trust among users while using any ready-made boilerplate such as useSAASkit. However, at any time, one can perfectly build their solution also customized solely integrating the necessary 2FA mechanisms.
Frequently asked questions
What is 2FA, which is Two Factor Authentication?
Two-factor authentication is the security process where users must provide two forms of identification: something they know (password) and something they have (knowledge of OTP or authenticator app).
Why Should I Implement 2FA to My SaaS App?
2FA will add another level of protection so that we can always reduce the chances our accounts will be accessed by unauthorized users, while also giving some assurance to the users.
Would it be possible to develop the Google Authenticator into my Next.js app?
Put simply - yes, you can use field libraries like speakeasy to integrate the use of Google Authenticator in TOTP 2FA setups.
What could be considered for choosing between SMS and authenticator app based 2FA?
Authenticator apps like Google Authenticator are deemed more secure from an overall security standpoint, but SMS-2FA might seem convenient to meet the requirements of some users with as few changes as possible.
Do I have to have 2FA in all of my apps, if indeed it is a SaaS app?
No, 2FA is not mandatory when we use SaaS Apps, but there are some considerations against that sentiment, on account of the type of data such apps handle.